1.Masalah jaringan karena kegagalan piranti jaringan
Skala gangguan akibat dari kegagalan piranti jaringan juga bisa bervariasi, dari hanya sebuah komputer karena kegagalan NIC – lan card; beberapa komputer karena kegagalan switch; atau bahkan berskala luas karena kegagalan pada switch central yang menghubungkan jaringan server. Untuk kegagalan lan card di salah satu komputer bisa diganti dengan network card cadangan anda.
Terus bagaimana kalau kegagalan jaringan itu akibat kerusakan pada switch? Design anda mengenai redundansi jaringan akan sangat membantu dalam menyelamatkan kegagalan jaringan anda. Kebutuhan load balancing dan redundansi haruslah dikaji untuk setiap kebutuhan berdasarkan penggunaan link redundansi; piranti router; switch dan multi-homed host yang bersifat kritis. Tujuan dari system redundansi ini dimaksudkan untuk menjamin ketersediaan layanan dimana tidak ada satupun titik rawan kegagalan.
2.Hal yang perlu di upgrade yaitu Masalah jaringan karena kegagalan kabel jaringan
Yang ini merupakan masalah jaringan yang umum kita temui akibat putusnya kabel jaringan yang bisa mempengaruhi kinerja sebuah komputer dalam jaringan karena putusnya kabel patch anda karena digigit tikus; masalah jaringan yang berdampak pada satu blok gedung karena putusnya kabel antar switch (uplink cable); atau bahkan berdampak pada sebagian besar komputer dalam jaringan lan anda karena kegagalan backbone cable.
3.anti virus perlu diupgrade untuk memperlancar jaringan.
Jumat, 31 Desember 2010
Kamis, 02 Desember 2010
Lab 3.4.3 Part B: Configuring Inter-VLAN Routing
Step 1: Connect the equipment
Step 2: Perform basic configurations on the router
Step 3: Configure VLAN trunking on the router
Step 4: .Configure Switch 1
Are all other switch ports in VLAN 1?
Which switch ports are in VLAN 10?
Which switch ports are in VLAN 20?
Issue the command show vlan.
What difference is noticed between the two commands show vlan brief and show vlan?
Step 5: Configure VLAN trunking on Switch 1
Which interfaces on Switch 1 are in trunk mode?
Which VLANs are allowed and active in the management domain?
Step 6: Configure VTP on Switch 1
Step 7: Configure Switch 2
Step 8: Configure VLAN trunking on Switch 2
Step 9: Configure VTP on Switch 2
Switch2(config)#vtp mode client
From Switch 2, verify that all VLANs have been propagated across the domain by issuing the command show vtp status.
What is the VTP version used on Switch 2?
What is the maximum VLANs supported locally?
What VTP operating mode is used on Switch 2?
What is the VTP domain name?
How did Switch 2 learn the domain name and VLAN information?
Step 10: Verify connectivity
The router and switches should be able to ping the interfaces of the other devices.
a. From each device, issue a ping to all interfaces.
Are the router pings successful?
b. From Switch 1, ping to all other devices.
Are Switch 1 pings successful?
From Switch 2, ping to all other devices.
Are Switch 2 pings successful? __________ If the ping is not successful, verify the connections and configurations again. Check to ensure that all cables are correct and that connections are seated. Check the router and switch configurations.
Step 11: Reflection
a. Why would VLANs be configured in a network?
b. Why would a VLAN benefit from trunking?
c. Why should VTP be used?
d. Which device provides connectivity between different VLANs?
e. What are some benefits of VLANs?
Lab 3.4.3 Part A: Configuring Inter-VLAN Routing
Step 1: Connect the equipment
Step 2: Perform basic configurations on the router
Step 3: Configure Fast Ethernet connections for each VLAN on the router
Step 4: Configure Switch 1
Step 5: Configure Switch 2
Step 6: Configure Switch 3
Step 7: Configure Host 1
Step 8: Configure Host 2
Step 9: Configure Host 3
Step 10: Configure the server
Step 11: Verify connectivity
The router should be able to ping the interfaces of the other devices.
a. From the router, issue a ping to Host 1.
Is the ping successful?
b. From the router, issue a ping to Host 2.
Is the ping successful?
c. From the router, issue a ping to Host 3.
Is the ping successful?
d. From the router, issue a ping to the server.
Is the ping successful?
Host 1 should be able to ping all other devices.
a. From Host 1, ping Host 2.
Is the ping successful?
b. From Host 1, ping the server.
Is the ping successful?
Why can Host 1 ping the server?
c. From the server, ping Host 1.
Is the ping successful?
d. From Switch 3, issue the command show spanning-tree.
Which ports are being used on Switch 3?
What is the role of each of these ports?
Which switch is acting as the root?
What is the protocol that allows VLANs to communicate without switching loops?
Step 12: Reflection
a. Why does this topology not scale well?
b. Why would a VLAN benefit from trunking?
c. Which device provides connectivity between different VLANs?
Kamis, 25 November 2010
CCNA2 Chapter 8
Lab 8.1.3 Security local data and transmitted data
Part 1
Step 1: secure bobs files folder
Step 2: test joes access to bobs files
Part 2
Step 1: identify a secure web page
Step 2: examine secure access to an untrusted source warming
Lab 8.2.1 planning for access lists and port filters
Step 1: Restrict Client A to one subnet
You are asked to restrict client A to only the subnet to which it is currently attached. Client A needs to be able to access server A. but it does not need to accsess the internet or server B. where would you place the access list?
Router | Interface | Allow or Deny? | Input or output filter? | Why? |
Router 2 | 0/0 dan 0/1 | deny | input | Karena hanya untuk mengekses server yang berada di internal jaringan dan tidak bisa untuk eksternal jaringan atau jaringan luar |
Step 2: Restrict client A access to server A but allow access to server B the internet
You are asked to restrict client B from accessing server B needs internet access and access to server B. where would you place the access list?
Router | Interface | Allow or Derry? | Input or output filter? | Why? |
Router 1 dan 3 | 0/0 dan 0/1 | allow | output | Karena diizinkan untu mengakses jaringan internal dan eksternal |
Step 3: Allow only client A to access the routers using only SSH
You have been asked to secure access to the routers for only client A. which will be the management PC for those routers. You want to limit access to only SSH from Client A and prevent telnet access. Where would you place the access list?
Router | Interface | Input or output filter? | Port | Allow or Deny? | Why? |
Router 1 | 0/0 dan 0/1 | input | 0 | deny | Jaringan internal |
Router 2 | 0/0 dan 0/1 | output | 0 | allow | Jaringan eksternal |
Router3 | 0/0 dan 0/1 | output | 0 | allow | Jaringan eksternal |
Lab 8.2.5 Researching an Anti-X Software Product
Step 1: identify three products
Company | Product |
smadav | Smadav |
morphic | Morposh |
Avira | Avira |
Step 2: Compare pricing
Company | Product | Price |
microsoft | Windows | Rp.1.500.000 |
Linux | free | |
aple | machintosh | Rp.5.000.000 |
Lab 8.3.1 Interpreting a service level agreement
Step 1: review typical customer needs
Step 2: Analyze a sample SLA and identify key components
a. Read over the sample SLA that follows and answer these questions regarding content, ISP responsibilities, and customer requirements.
b. According to this agreement, can the ISP be held liable for damage to equipment owned by the customer [Client] or data loss that occurs due to accidental actions by ISP vendor staff or other persons? bisa
c. What are some examples of One Time Services included in the SLA? E-mail service, electronic interchange, online accounting, secure remote workerr support, remote indtrumentation and control system, and backup and recovery service.
d. What are some examples of On going Services included in the SLA? E-mail service, online acounting
e. When will regular downtime maintenance be scheduled and how many business days notice must the ISP give of any scheduled downtime? Banyak jam dalam satu hari dan banyak hari dalam senulan.What does the ISP’s network monitoring system do when an error condition is detected? What is the stated availability of the Systems Administrators in the event of a system failure? What is “usage monitoring” and how does the ISP provide this service? Dengan memantau kerja sistem
f. Regarding problem severity and ISP response time, what is the difference in response between “Level 1 – normal business hours” and “Level 3 – normal business hours”? pada level satu baru mendeteksi problem dan pada level 3 sudah ada pengontrolan
g. On what factors are the penalties for service outages based? Provides an estimate for the cost to the customer for a service outage for each of the services the customer wants covered by an SLA.
Lab 8.3.2 conducting a Network capture with wireshark
Step 1: install and launch Wireshark
Step 2: select an interface to use for capturing pakets
Step 3 : Analysyze web trafict information (optional)
a. The conection to the google server with a query to the DNS server to lookup the server IP address. The destination server IP address will most likely start with 64.x.x.x what is the source and destination of the first packet sent to the google server?
Source: 192.168.1.103
Destination: 65.24.7.3
b. Open another browser window and go to the ARIN who is database http://www.arin .net/whois/ or use another whois lookup tool and enter thr IP address of the destination server. To what organization is this IP address assigned? 192.168.1.103
c. What are the protocols is used to establish the connection to the web server and deliver the web page to your local host? TCP
d. What is the color used to establish the connection to the server and deliver the web page to your local host? hijau
e. What is the color used to highlight the traffic between your host and the google web server? gray
Step 5: filter a network capture
a. Open a command prompt window by clicking start > all programs > run and typing cmd.
b. Ping a host IP address on your local network and observer? ICMP
c. When icmp is typed in the filter text box what kind of raffic is was displayed? Ketika kita menge-ping host IP address yang ada di jaringan local kita
d. Click the filter: Expression button on the wireshark eindow. Scroll down the list and view the filter possibilities there. Are TCP, HTTP,ARP and other protocols listed? Ya ada
Step 6:reflection
a. There are hundreads of filters listed in the filter: expression option. It may be possible that, in a large network , there would be enormounts and many different types of traffic. Which three filters in the long list do you think might be most useful to a network administrator
b. Is wreshark a tool for out of band or in band network monitoring
Explain your answare
Lab 8.4.2 planning a backup solution
step 1: choose the media and backup hardware
Equipment / media | price | quality |
USB and solid-state drives | $30-$90 | medium |
fireWire drives | $180 | best |
CD-RW and DVD+RW/-RW drives | $100 | medium |
Step 2: design a backup plan and procedure
a. Describe the equipment recommended and explain why you selected this equipment
Saya memilih media di atas Karena saya melihat dari segi kapasitas dan segi ekonomis
b. Describe location of the equipment in the network and the network link speeds to the equipment
c. Describe the backup media to be used and also explain why you selected this media
d. Describe the backup schedule
e. Describe the backup and restore procedure, including what kind of backup (Normal, differential, incremental), how it will be tested what kind of maintenance the equipment requires. How tapes will be labeled and where tapes that have been backed up will be stored. When backups need to be restored, what is the procedure for a file a folder a driver (use extra sheets it necessary)
CCNA Discovery 3 Module 3
1.
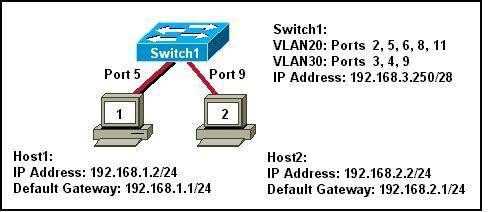
Refer to the exhibit. What two statements can be concluded from the information that is shown in the exhibit? (Choose two.)
• All ports that are listed in the exhibit are access ports.
• ARP requests from Host1 will be forwarded to Host2.
• Attaching Host1 to port 3 will automatically allow communication between both hosts.
• The default gateway for each host must be changed to 192.168.3.250/28 to allow communication between both hosts.
• A router connected to the switch is needed to forward traffic between the hosts.
2.
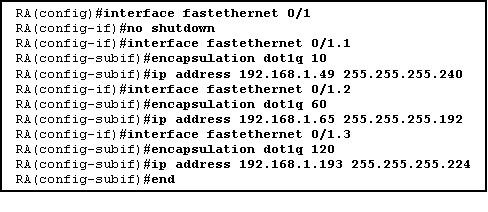
A router is configured to connect to a trunked uplink as shown in the exhibit. A packet is received on the FastEthernet 0/1 physical interface from VLAN 10. The packet destination address is 192.168.1.120. What will the router do with this packet?
• The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
• The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
• The router will not process the packet since the source and destination are on the same subnet.
• The router will drop the packet since no network that includes the source address is attached to the router.

A router is configured to connect to a trunked uplink as shown in the exhibit. A packet is received on the FastEthernet 0/1 physical interface from VLAN 10. The packet destination address is 192.168.1.120. What will the router do with this packet?
• The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
• The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
• The router will not process the packet since the source and destination are on the same subnet.
• The router will drop the packet since no network that includes the source address is attached to the router.
3. The information contained in a BPDU is used for which two purposes? (Choose two.)
• to prevent loops by sharing bridging tables between connected switches
• to set the duplex mode of a redundant link
• to determine the shortest path to the root bridge
• to determine which ports will forward frames as part of the spanning tree
• to activate looped paths throughout the network
• to prevent loops by sharing bridging tables between connected switches
• to set the duplex mode of a redundant link
• to determine the shortest path to the root bridge
• to determine which ports will forward frames as part of the spanning tree
• to activate looped paths throughout the network
4. A router has two serial interfaces and two Fast Ethernet interfaces. This router must be connected to a WAN link and to a switch that supports four VLANs. How can this be accomplished in the most efficient and cost-effective manner to support inter-VLAN routing between the four VLANs?
• Connect a smaller router to the serial interface to handle the inter-VLAN traffic.
• Add two additional Fast Ethernet interfaces to the router to allow one VLAN per interface.
• Connect a trunked uplink from the switch to one Fast Ethernet interface on the router and create logical subinterfaces for each VLAN.
• Use serial-to-Fast Ethernet transceivers to connect two of the VLANs to the serial ports on the router. Support the other two VLANs directly to the available FastEthernet ports.
• Connect a smaller router to the serial interface to handle the inter-VLAN traffic.
• Add two additional Fast Ethernet interfaces to the router to allow one VLAN per interface.
• Connect a trunked uplink from the switch to one Fast Ethernet interface on the router and create logical subinterfaces for each VLAN.
• Use serial-to-Fast Ethernet transceivers to connect two of the VLANs to the serial ports on the router. Support the other two VLANs directly to the available FastEthernet ports.
5. When are MAC addresses removed from the CAM table?
• at regular 30 second intervals
• when a broadcast packet is received
• when the IP Address of a host is changed
• after they have been idle for a certain period of time
• at regular 30 second intervals
• when a broadcast packet is received
• when the IP Address of a host is changed
• after they have been idle for a certain period of time
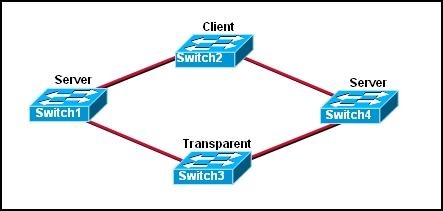
6.
Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches. Which two are possible reasons for this? (Choose two.)
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.

Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches. Which two are possible reasons for this? (Choose two.)
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.
7. Which three must be used when a router interface is configured for VLAN trunking? (Choose three.)
• one subinterface per VLAN
• one physical interface for each subinterface
• one IP network or subnetwork for each subinterface
• one trunked link per VLAN
• a management domain for each subinterface
• a compatible trunking protocol encapsulation for each subinterface
• one subinterface per VLAN
• one physical interface for each subinterface
• one IP network or subnetwork for each subinterface
• one trunked link per VLAN
• a management domain for each subinterface
• a compatible trunking protocol encapsulation for each subinterface
Refer to the exhibit. The switches are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
• VLANs cannot be created on transparent mode switches.
• Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
• VLANs created on transparent mode switches are not included in VTP advertisements.
• There are no ports assigned to the new VLAN on the other switches.
• Transparent mode switches do not forward VTP advertisements.
9. Which two criteria are used by STP to select a root bridge? (Choose two.)
• memory size
• bridge priority
• switching speed
• number of ports
• base MAC address
• switch location
• memory size
• bridge priority
• switching speed
• number of ports
• base MAC address
• switch location
10. Which three steps should be taken before moving a Catalyst switch to a new VTP management domain? (Choose three.)
• Reboot the switch.
• Reset the VTP counters to allow the switch to synchronize with the other switches in the domain.
• Download the VTP database from the VTP server in the new domain.
• Configure the VTP server in the domain to recognize the BID of the new switch.
• Select the correct VTP mode and version.
• Configure the switch with the name of the new management domain.
• Reboot the switch.
• Reset the VTP counters to allow the switch to synchronize with the other switches in the domain.
• Download the VTP database from the VTP server in the new domain.
• Configure the VTP server in the domain to recognize the BID of the new switch.
• Select the correct VTP mode and version.
• Configure the switch with the name of the new management domain.
11. Which two items will prevent broadcasts from being sent throughout the network? (Choose two.)
• bridges
• routers
• switches
• VLANs
• hubs
• bridges
• routers
• switches
• VLANs
• hubs
12. Which two characteristics describe a port in the STP blocking state? (Choose two.)
• provides port security
• displays a steady green light
• learns MAC addresses as BPDUs are processed
• discards data frames received from the attached segment
• receives BPDUs and directs them to the system module
• provides port security
• displays a steady green light
• learns MAC addresses as BPDUs are processed
• discards data frames received from the attached segment
• receives BPDUs and directs them to the system module
13. What is the first step in the process of convergence in a spanning tree topology?
• election of the root bridge
• determination of the designated port for each segment
• blocking of the non-designated ports
• selection of the designated trunk port
• activation of the root port for each segment
• election of the root bridge
• determination of the designated port for each segment
• blocking of the non-designated ports
• selection of the designated trunk port
• activation of the root port for each segment
14. In which STP state does a switch port transmit user data and learn MAC addresses?
• blocking
• learning
• disabling
• listening
• forwarding
• blocking
• learning
• disabling
• listening
• forwarding
15. What is the purpose of VTP?
• maintaining consistency in VLAN configuration across the network
• routing frames from one VLAN to another
• routing the frames along the best path between switches
• tagging user data frames with VLAN membership information
• distributing BPDUs to maintain loop-free switched paths
• maintaining consistency in VLAN configuration across the network
• routing frames from one VLAN to another
• routing the frames along the best path between switches
• tagging user data frames with VLAN membership information
• distributing BPDUs to maintain loop-free switched paths
16. Which statement best describes adaptive cut-through switching?
• The switch initially forwards all traffic using cut-through switching and then changes to store-and-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then changes to fast-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then temporarily disables the port if errors exceed a threshold value.
• The switch initially forwards all traffic using store-and-forward switching and then changes to cut-through switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then changes to store-and-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then changes to fast-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then temporarily disables the port if errors exceed a threshold value.
• The switch initially forwards all traffic using store-and-forward switching and then changes to cut-through switching if errors exceed a threshold value.
17. Using STP, how long does it take for a switch port to go from the blocking state to the forwarding state?
• 2 seconds
• 15 seconds
• 20 seconds
• 50 seconds
• 2 seconds
• 15 seconds
• 20 seconds
• 50 seconds
18.
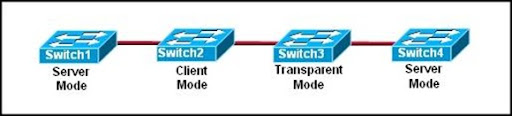
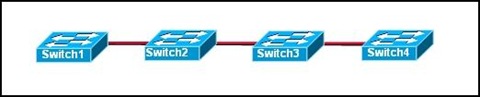
Refer to the exhibit. The switches are interconnected by trunked links and are configured for VTP as shown. A new VLAN is added to Switch1. Which three actions will occur? (Choose three.)
• Switch1 will not add the VLAN to its database and will pass the update to Switch 2.
• Switch2 will add the VLAN to its database and pass the update to Switch3.
• Switch3 will pass the VTP update to Switch4.
• Switch3 will add the VLAN to its database.
• Switch4 will add the VLAN to its database.
• Switch4 will not receive the update.

Refer to the exhibit. The switches are interconnected by trunked links and are configured for VTP as shown. A new VLAN is added to Switch1. Which three actions will occur? (Choose three.)
• Switch1 will not add the VLAN to its database and will pass the update to Switch 2.
• Switch2 will add the VLAN to its database and pass the update to Switch3.
• Switch3 will pass the VTP update to Switch4.
• Switch3 will add the VLAN to its database.
• Switch4 will add the VLAN to its database.
• Switch4 will not receive the update.
19. Which Catalyst feature causes a switch port to enter the spanning-tree forwarding state immediately?
• backbonefast
• uplinkfast
• portfast
• rapid spanning tree
• backbonefast
• uplinkfast
• portfast
• rapid spanning tree
20.

Refer to the exhibit. Which set of commands would be used on the router to provide communication between the two hosts connected to the switch?
• Router(config)# interface vlan 2
Router(config-if)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface vlan 3
Router(config-if)# ip address 192.168.3.1 255.255.255.0
Router(config-if)# no shutdown
• Router(config)# interface fastethernet 0/0
Router(config-if)# no shutdown
Router(config-if)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 2
Router(config-subif)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# interface fastethernet 0/0.3
Router(config-subif)# encapsulation dot1q 3
Router(config-subif)# ip address 192.168.3.1 255.255.255.0
• Router(config)# interface vlan 2
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface vlan 3
Router(config-if)# switchport mode trunk dot1q
• Router(config)# interface fastethernet 0/0
Router(config-if)# mode trunk dot1q 2 3
Router(config-if)# ip address 192.168.2.1 255.255.255.0v

Refer to the exhibit. Which set of commands would be used on the router to provide communication between the two hosts connected to the switch?
• Router(config)# interface vlan 2
Router(config-if)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface vlan 3
Router(config-if)# ip address 192.168.3.1 255.255.255.0
Router(config-if)# no shutdown
• Router(config)# interface fastethernet 0/0
Router(config-if)# no shutdown
Router(config-if)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 2
Router(config-subif)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# interface fastethernet 0/0.3
Router(config-subif)# encapsulation dot1q 3
Router(config-subif)# ip address 192.168.3.1 255.255.255.0
• Router(config)# interface vlan 2
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface vlan 3
Router(config-if)# switchport mode trunk dot1q
• Router(config)# interface fastethernet 0/0
Router(config-if)# mode trunk dot1q 2 3
Router(config-if)# ip address 192.168.2.1 255.255.255.0v
Kamis, 11 November 2010
CCNA Discovery 2 Module 5 Exam
1. vIn what two ways does SDM differ from the IOS CLI? (Choose two.)
• SDM is used for in-band management only. The IOS CLI can be used for in-band and out-of-band management.
• SDM is accessed through a Telnet application. The IOS CLI is accessed through a web browser.
• SDM is available for all router platforms. The IOS CLI is available for a limited number of Cisco devices.
• SDM utilizes GUI buttons and text boxes. The IOS CLI requires the use of text-based commands.
• SDM is used for advanced configuration tasks. The IOS CLI is preferred for initial basic device configuration.
2. Which mode will a configured router display at login?
• global configuration mode
• setup mode
• ROM monitor mode
• user EXEC mode
• SDM is used for in-band management only. The IOS CLI can be used for in-band and out-of-band management.
• SDM is accessed through a Telnet application. The IOS CLI is accessed through a web browser.
• SDM is available for all router platforms. The IOS CLI is available for a limited number of Cisco devices.
• SDM utilizes GUI buttons and text boxes. The IOS CLI requires the use of text-based commands.
• SDM is used for advanced configuration tasks. The IOS CLI is preferred for initial basic device configuration.
2. Which mode will a configured router display at login?
• global configuration mode
• setup mode
• ROM monitor mode
• user EXEC mode
3. Refer to the exhibit. Which password or passwords will be encrypted as a result of the configuration that is shown?
• virtual terminal only
• enable mode only
• console and virtual terminal only
• enable mode and virtual terminal
• only the service password
• all configured passwords 4.Refer to the exhibit. Which three sets of commands are required to enable administrators to connect to the Switch1 console over Telnet for configuration and management? (Choose three.)
• Switch1(config)# interface fa0/1
Switch1(config-if)# ip address 192.168.2.64 255.255.255.192
• Switch1(config)# interface fa0/1
Switch1(config-if)# ip address 192.168.2.66 255.255.255.192
• Switch1(config)# interface vlan 1
Switch1(config-if)# ip address 192.168.2.126 255.255.255.192
Switch1(config-if)# no shutdown
• Switch1(config)# line vty 0 4
Switch1(config-line)# enable password cisco
Switch1(config-line)# login
• Switch1(config)# line vty 0 15
Switch1(config-line)# password cisco
Switch1(config-line)# login
• Switch1(config)# ip default-gateway 192.168.2.65
• virtual terminal only
• enable mode only
• console and virtual terminal only
• enable mode and virtual terminal
• only the service password
• all configured passwords 4.Refer to the exhibit. Which three sets of commands are required to enable administrators to connect to the Switch1 console over Telnet for configuration and management? (Choose three.)
• Switch1(config)# interface fa0/1
Switch1(config-if)# ip address 192.168.2.64 255.255.255.192
• Switch1(config)# interface fa0/1
Switch1(config-if)# ip address 192.168.2.66 255.255.255.192
• Switch1(config)# interface vlan 1
Switch1(config-if)# ip address 192.168.2.126 255.255.255.192
Switch1(config-if)# no shutdown
• Switch1(config)# line vty 0 4
Switch1(config-line)# enable password cisco
Switch1(config-line)# login
• Switch1(config)# line vty 0 15
Switch1(config-line)# password cisco
Switch1(config-line)# login
• Switch1(config)# ip default-gateway 192.168.2.65
5. How does the SYST LED on the catalyst 2960 switch indicate a POST failure?
• blinks rapidly amber
• blinks rapidly green
• steady amber
• steady green 6. Refer to the exhibit. A company always uses the last valid IP address in a subnetwork as the IP address of the router LAN interface. A network administrator is using a laptop to configure switch X with a default gateway. Assuming that the switch IP address is 192.168.5.147/24, what command will the administrator use to assign a default gateway to the switch?
• X(config)# ip default-gateway 192.168.5.254
• X(config)# ip gateway 192.168.5.1
• X(config)# ip route 0.0.0.0 0.0.0.0 192.168.5.1
• X(config)# ip default-route 192.168.5.1
• X(config)# ip route 192.168.5.254 255.255.255.0 fastethernet 0/0
7. A technician has made changes to the configuration of a router. What command will allow the technician to view the current configuration before he saves the changes?
• router# show running-config
• router# show startup-config
• router# show flash
• router# show version
8. Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
• VTY interface
• console interface
• Ethernet interface
• secret EXEC mode
• privileged EXEC mode
• router configuration mode
9. To save time, IOS commands may be partially entered and then completed by typing which key or key combination?
• Tab
• Ctrl-P
• Ctrl-N
• Up Arrow
• Right Arrow
• Down Arrow
10. What is the correct command sequence to configure a router host name to ‘LAB_A’?
• Router> enable
Router# configure terminal
Router(config)# hostname LAB_A
• Router> enable
Router# hostname LAB_A
• Router> enable
Router# configure router
Router(config)# hostname LAB_A
• Router> enable
Router(config)# host name LAB_A
11. Refer to the exhibit. From the router console, an administrator is unable to ping a Catalyst switch that is located in another building. What can the administrator do from her location to check the IP configuration of the attached switch?
• Open an SDM session with the switch from her desktop.
• Telnet to the switch from the router console.
• Use the show cdp neighbors detail command from the router console.
• The administrator must go to the switch location and make a console connection to check these settings.
12. Which two options must be selected in SDM Express to enable a router serial interface to obtain an IP address automatically? (Choose two.)
• Easy IP (IP negotiated)
• IP unnumbered
• No IP address
• HDLC encapsulation
• Frame Relay encapsulation
• PPP encapsulation
• blinks rapidly amber
• blinks rapidly green
• steady amber
• steady green 6. Refer to the exhibit. A company always uses the last valid IP address in a subnetwork as the IP address of the router LAN interface. A network administrator is using a laptop to configure switch X with a default gateway. Assuming that the switch IP address is 192.168.5.147/24, what command will the administrator use to assign a default gateway to the switch?
• X(config)# ip default-gateway 192.168.5.254
• X(config)# ip gateway 192.168.5.1
• X(config)# ip route 0.0.0.0 0.0.0.0 192.168.5.1
• X(config)# ip default-route 192.168.5.1
• X(config)# ip route 192.168.5.254 255.255.255.0 fastethernet 0/0
7. A technician has made changes to the configuration of a router. What command will allow the technician to view the current configuration before he saves the changes?
• router# show running-config
• router# show startup-config
• router# show flash
• router# show version
8. Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
• VTY interface
• console interface
• Ethernet interface
• secret EXEC mode
• privileged EXEC mode
• router configuration mode
9. To save time, IOS commands may be partially entered and then completed by typing which key or key combination?
• Tab
• Ctrl-P
• Ctrl-N
• Up Arrow
• Right Arrow
• Down Arrow
10. What is the correct command sequence to configure a router host name to ‘LAB_A’?
• Router> enable
Router# configure terminal
Router(config)# hostname LAB_A
• Router> enable
Router# hostname LAB_A
• Router> enable
Router# configure router
Router(config)# hostname LAB_A
• Router> enable
Router(config)# host name LAB_A
11. Refer to the exhibit. From the router console, an administrator is unable to ping a Catalyst switch that is located in another building. What can the administrator do from her location to check the IP configuration of the attached switch?
• Open an SDM session with the switch from her desktop.
• Telnet to the switch from the router console.
• Use the show cdp neighbors detail command from the router console.
• The administrator must go to the switch location and make a console connection to check these settings.
12. Which two options must be selected in SDM Express to enable a router serial interface to obtain an IP address automatically? (Choose two.)
• Easy IP (IP negotiated)
• IP unnumbered
• No IP address
• HDLC encapsulation
• Frame Relay encapsulation
• PPP encapsulation
13. What three settings can be made in the SDM Express basic configuration screen? (Choose three.)
• host name
• DHCP options
• domain name
• interface IP addresses
• enable secret password
• DNS server IP addresses 14. Which tasks can be accomplished by using the command history feature? (Choose two.)
• View a list of commands entered in a previous session.
• Recall up to 15 command lines by default.
• Set the command history buffer size.
• Recall previously entered commands.
• Save command lines in a log file for future reference.
15. What option within Cisco SDM Express must be configured to allow hosts that receive IP address settings from the router to resolve names on the network or Internet?
• host name
• domain name
• DHCP address pool
• DNS server IP address
16. Which three encapsulation types can be set on a serial interface by an administrator who is using SDM Express? (Choose three.)
• ATM
• CHAP
• Frame Relay
• HDLC
• PAP
• PPP
17. Which command will display routing table information about all known networks and subnetworks?
• Router# show ip interfaces
• Router# show ip connections
• Router# show ip route
• Router# show ip networks
18. A network administrator needs to configure a router. Which of the following connection methods requires network functionality to be accessible?
• console
• AUX
• Telnet
• modem
19. Which three pieces of information about a neighbor device can be obtained by the show cdp neighbors command? (Choose three.)
• platform
• routing protocol
• connected interface of neighbor device
• device ID
• IP addresses of all interfaces
• enable mode password
20.Which function is a unique responsibility of the DCE devices shown in the exhibit?
• transmission of data
• reception of data
• clocking for the synchronous link
• noise cancellation in transmitted data
21. Which of the following are functions of NVRAM? (Choose two.)
• stores the routing table
• retains contents when power is removed
• stores the startup configuration file
• contains the running configuration file
• stores the ARP table
22. Refer to the exhibit. Which series of commands will enable users who are attached to Router1 to access the remote server?
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.129 255.255.255.252
Router1(config-if)# clock rate 64000
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.125 255.255.255.252
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.125 255.255.255.252
Router1(config-if)# clock rate 64000
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.129 255.255.255.252
Router1(config-if)# no shutdown
23. A network technician is attempting to add an older workstation to a Cisco switched LAN. The technician has manually configured the workstation to full-duplex mode in order to enhance the network performance of the workstation. However, when the device is attached to the network, performance degrades and excess collision are detected. What is the cause of this problem?
• The host is configured in a different subnet from the subnet of the switch.
• There is a duplex mismatch between the workstation and switch port.
• The switch port is running at a different speed from the speed of the workstation NIC.
• The host has been configured with a default gateway that is different from that of the switch.
24. Which of the following statements are true regarding the user EXEC mode? (Choose two.)
• All router commands are available.
• Global configuration mode can be accessed by entering the enable command.
• A password can be entered to allow access to other modes.
• Interfaces and routing protocols can be configured.
• Only some aspects of the router configuration can be viewed.
25. Which command turns on a router interface?
• Router(config-if)# enable
• Router(config-if)# no down
• Router(config-if)# s0 active
• Router(config-if)# interface up
• Router(config-if)# no shutdown
• host name
• DHCP options
• domain name
• interface IP addresses
• enable secret password
• DNS server IP addresses 14. Which tasks can be accomplished by using the command history feature? (Choose two.)
• View a list of commands entered in a previous session.
• Recall up to 15 command lines by default.
• Set the command history buffer size.
• Recall previously entered commands.
• Save command lines in a log file for future reference.
15. What option within Cisco SDM Express must be configured to allow hosts that receive IP address settings from the router to resolve names on the network or Internet?
• host name
• domain name
• DHCP address pool
• DNS server IP address
16. Which three encapsulation types can be set on a serial interface by an administrator who is using SDM Express? (Choose three.)
• ATM
• CHAP
• Frame Relay
• HDLC
• PAP
• PPP
17. Which command will display routing table information about all known networks and subnetworks?
• Router# show ip interfaces
• Router# show ip connections
• Router# show ip route
• Router# show ip networks
18. A network administrator needs to configure a router. Which of the following connection methods requires network functionality to be accessible?
• console
• AUX
• Telnet
• modem
19. Which three pieces of information about a neighbor device can be obtained by the show cdp neighbors command? (Choose three.)
• platform
• routing protocol
• connected interface of neighbor device
• device ID
• IP addresses of all interfaces
• enable mode password
20.Which function is a unique responsibility of the DCE devices shown in the exhibit?
• transmission of data
• reception of data
• clocking for the synchronous link
• noise cancellation in transmitted data
21. Which of the following are functions of NVRAM? (Choose two.)
• stores the routing table
• retains contents when power is removed
• stores the startup configuration file
• contains the running configuration file
• stores the ARP table
22. Refer to the exhibit. Which series of commands will enable users who are attached to Router1 to access the remote server?
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.129 255.255.255.252
Router1(config-if)# clock rate 64000
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.125 255.255.255.252
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.125 255.255.255.252
Router1(config-if)# clock rate 64000
Router1(config-if)# no shutdown
• Router1(config)# interface S0/0/0
Router1(config-if)# ip address 64.100.0.129 255.255.255.252
Router1(config-if)# no shutdown
23. A network technician is attempting to add an older workstation to a Cisco switched LAN. The technician has manually configured the workstation to full-duplex mode in order to enhance the network performance of the workstation. However, when the device is attached to the network, performance degrades and excess collision are detected. What is the cause of this problem?
• The host is configured in a different subnet from the subnet of the switch.
• There is a duplex mismatch between the workstation and switch port.
• The switch port is running at a different speed from the speed of the workstation NIC.
• The host has been configured with a default gateway that is different from that of the switch.
24. Which of the following statements are true regarding the user EXEC mode? (Choose two.)
• All router commands are available.
• Global configuration mode can be accessed by entering the enable command.
• A password can be entered to allow access to other modes.
• Interfaces and routing protocols can be configured.
• Only some aspects of the router configuration can be viewed.
25. Which command turns on a router interface?
• Router(config-if)# enable
• Router(config-if)# no down
• Router(config-if)# s0 active
• Router(config-if)# interface up
• Router(config-if)# no shutdown
CCNA Discovery 2 Module 4 Exam
1. In an 8 bit binary number, what is the total number of combinations of the eight bits?
• 128
• 254
• 255
• 256
• 512
• 1024
2. Convert the decimal number 231 into its binary equivalent. Select the correct answer from the list below.• 128
• 254
• 255
• 256
• 512
• 1024
• 11110010
• 11011011
• 11110110
• 11100111
• 11100101
• 11101110
3. How many usable hosts are available given a Class C IP address with the default subnet mask?
• 254
• 255
• 256
• 510
• 511
• 512
4. Which statement describes NAT overload or PAT?
• Each internal address is dynamically translated to an individual external IP address.
• A single internal address is always translated to the same unique external IP address.
• Many internal addresses can be translated to a single IP address using different port assignments.
• Many internal addresses are statically assigned a single IP address and port to use for communications.
5. Which IPv4 class of addresses provides the most networks?
• Class A
• Class B
• Class C
• Class D
• Class E
6. Which statement accurately describes public IP addresses?
• Public addresses cannot be used within a private network.
• Public IP addresses must be unique across the entire Internet.
• Public addresses can be duplicated only within a local network.
• Public IP addresses are only required to be unique within the local network.
• Network administrators are free to select any public addresses to use for network devices that access the Internet.
7. Which two statements describe classful IP addresses? (Choose two.)
• It is possible to determine which class an address belongs to by reading the first bit.
• The number of bits used to identify the hosts is fixed by the class of the network.
• Only Class A addresses can be represented by high-order bits 100.
• Up to 24 bits can make up the host portion of a Class C address.
• Up to 24 bits can be used to identify unique networks.
• Three of the five classes of addresses are reserved for multicasts and experimental use.
8. Company XYZ uses a network address of 192.168.4.0. It uses the mask of 255.255.255.224 to create subnets. What is the maximum number of usable hosts in each subnet?
• 6
• 14
• 30
• 62
9. hat is the network broadcast address for a Class C address of 192.168.32.0 with the default subnet mask?
• 192.168.0.0
• 192.168.0.255
• 192.168.32.0
• 192.168.32.254
• 192.168.32.255
10.
Refer to the exhibit. Host A is connected to the LAN, but it cannot get access to any resources on the Internet. The configuration of the host is shown in the exhibit. What could be the cause of the problem?
• The host subnet mask is incorrect.
• The default gateway is a network address.
• The default gateway is a broadcast address.
• The default gateway is on a different subnet from the host.
11. IPv6 increases the IP address size from 32 bits to how many bits?
• 64
• 96
• 128
• 192
• 256
• 512
12. What is the range of the first octet in a Class B address?
• 127 to 191
• 127 to 192
• 128 to 191
• 128 to 192
13. Which IPv4 class provides the highest number of host addresses per network?
• Class A
• Class B
• Class C
• Class D
• Class E
14.
refer to the exhibit. Which range of IP addresses would allow hosts that are connected to the Router1 Fa0/0 interface to access outside networks?
• 192.168.1.0 through 192.168.1.95
• 192.168.1.66 through 192.168.1.94
• 192.168.1.66 through 192.168.1.96
• 192.168.1.0 through 192.168.1.127
• 192.168.1.66 through 192.168.1.128
15. Which option shows the proper notation for an IPv6 address?
• 2001,0db8,3c55,0015,abcd,ff13
• 2001-0db8-3c55-0015-abcd-ff13
• 2001.0db8.3c55.0015.abcd.ff13
• 2001:0db8:3c55:0015::abcd:ff13
16. What are two reasons that NAT was developed? (Choose two.)
• to preserve registered public IP addresses
• to allow users on the public Internet to access local networks
• to provide a method for privately addressed LANs to participate in the Internet
• to make routing protocols operate more efficiently
• to allow private addresses to be routed on the public Internet
• to reduce overhead and CPU usage on gateway routers
17. What must happen for a privately addressed host on an inside local network to be able to communicate with an outside destination host on the Internet?
• The host IP address must be translated to an outside private address.
• The host IP address must be translated to an inside local address.
• The host IP address must be translated to an outside local address.
• The host IP address must be translated to an inside global address.
18. Which port numbers are used by PAT to create unique global addresses?
• 255 and below
• 1024 and below
• 1025 and above
• 64,000 and above
19. Static NAT works by mapping a specific inside local IP address to what other specific address type?
• inside global
• outside local
• outside global
• private IP address
20. What are three advantages of NAT implementations? (Choose three.)
• improved security
• improved router performance
• decreased processor load
• improved scalability
• universal application compatibility
• sharing few public IP addresses with many hosts
Langganan:
Postingan (Atom)